Cybercriminals and hackers are eager to acquire online passwords, especially as COVID-19 runs rampant and many organizations are attempting to push the majority of their business operations online. An unprotected password can allow cybercriminals to fraudulently gain access to systems, and the important data stored in those systems. Personally identifiable information (PII) is one type of data cybercriminals are always trying to find. PII is any data that could potentially identify a specific individual, including one’s SSN, date of birth, driver's license number and/or email address, to name a few. Protecting PII is essential for personal privacy, data privacy and protection, information privacy and information security. With just a few pieces of an individual's personal information, thieves can create false accounts in the person's name, incur debt, create a falsified passport or sell a person's identity to a criminal.
What is 2FA?
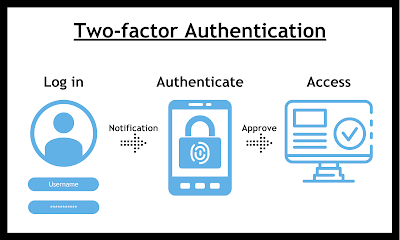
Two-factor authentication (2FA) is another method of identity validation layered on a traditional identity and password (lock and key) access method, which offers several benefits:
Provides an extra layer of security for individuals and systems where it has been applied, reducing the risk of unauthorized access.
Protects the people who have data in the system by allowing only those with legitimate business purposes to access that data, preventing criminals from using it for fraudulent purposes.
Ensures that you are the only person who can access your account, even if someone knows your password.
How does it work?
Two-factor authentication requires the additional step of entering a passcode along with a username and password, making it much more difficult for someone with bad intent to obtain login information and access the data of the clients you serve. There are multiple ways a passcode can be provided to staff, including through the vendor app, a text message, a phone call or through the use of a hardware token.
What is a hardware token?
Hardware tokens are physical devices, typically keychain-sized, that allow individuals to secure access systems remotely by generating an authentication key in the form of numbers or letters. Users input the key after an initial login to access the system.
Colorado, through the state’s Interoperability Program, is working on turning on 2FA for several state-run applications including The Child Care Automated Tracking System (CHATS), Colorado Child Welfare Training System (Trails), and the Colorado Benefits Management System (CBMS). Earlier this fall, 2FA was successfully turned on for Colorado’s Automated Child Support Enforcement System (ASCES).
Turning on two-factor authentication is just another step the state is taking to keep Coloradans’ data safe. It’s something that we encourage everyone to take advantage of to protect their own data with their personal email accounts, applications, online banking and everything in between.
Today’s blog comes from Megan Tobias, Communications Manager